Firewalls play a pivotal part in guarding networks from cyber pitfalls, yet numerous businesses still make preventable crimes in their setup and conservation. Whether you are managing a small office network or a large enterprise structure, your firewall must operate at peak effectiveness. thus, understanding the most common firewall miscalculations and how to fix them is essential for maintaining security, performance, and peace of mind.
1. Using dereliction Settings Without Customization
One of the most frequent firewall mistakes is counting on plant dereliction settings. These settings are frequently general and fail to address the specific requirements of your association. Also, hackers frequently know the dereliction configurations and target them to exploit vulnerabilities.
As a result, leaving your firewall in its dereliction state opens the door to gratuitous threat. To avoid this, incontinently change dereliction watchwords, configure custom rule sets, and regularly review access warrants for optimal protection.
2. Allowing Too numerous Open Ports
Every open ports on your firewall represents a implicit entry point for bushwhackers. While some ports are necessary for services like dispatch or train sharing, numerous systems run with far more open ports than needed. Accordingly, this increases the attack face and weakens your overall defense.
Also, directors occasionally open ports for temporary use and forget to close them latterly. To stay secure, regularly inspection all open ports, close any that aren’t in use, and document the purpose of each open port.
3. Failing to Implement Internal Firewalls
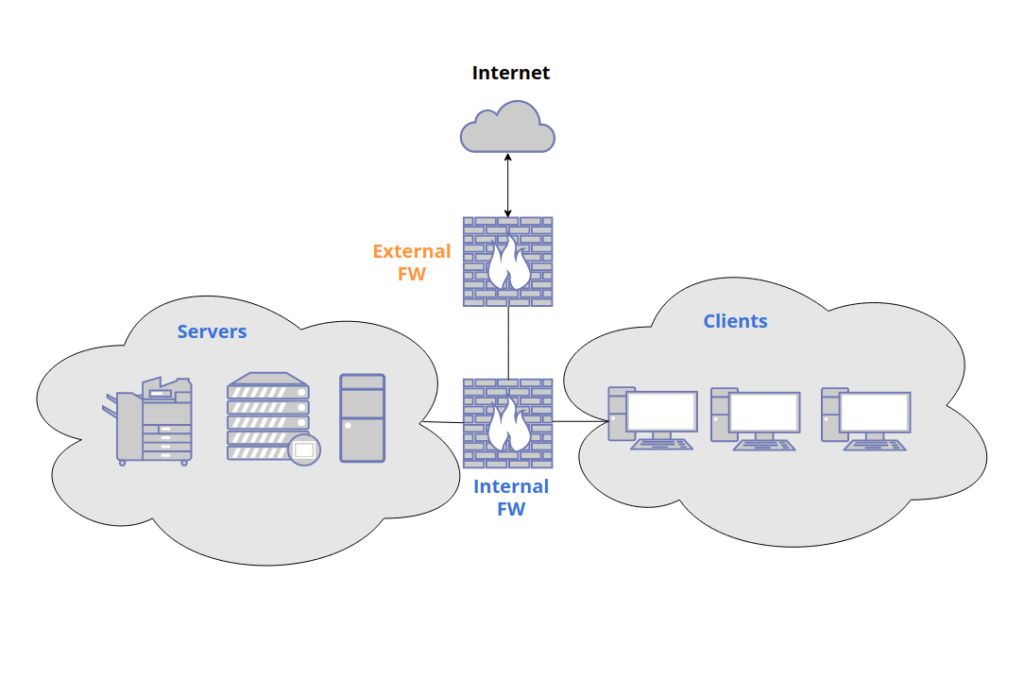
Numerous associations only emplace border firewalls, ignoring the need for internal segmentation. While a border firewall is essential, counting solely on it can lead to side movement by bushwhackers if a breach occurs. Likewise, malware can spread snappily between internal systems when there are no internal restrictions.
By segmenting your network with internal firewalls, you reduce the chances of a complete concession. For illustration, separate guest Wi- Fi, finance systems, and HR data using distinct zones and programs.
4. Not streamlining Firewall Firmware Regularly
Firewall merchandisers constantly release updates to patch vulnerabilities and ameliorate performance. still, numerous druggies detention or ignore these updates, leaving their systems exposed. Over time, outdated firmware can produce comity issues and increase the threat of exploitation.
Thus, set a regular update schedule and subscribe to seller cautions for critical patches. Also, test updates in a staging terrain to insure they don’t disrupt your network operations before deployment.
5. Overlooking Firewall Logs and cautions
Another critical mistake is ignoring or misruling firewall logs. These logs give precious perceptivity into suspicious conditioning, failed connection attempts, and unusual business patterns. Without monitoring, you miss early warning signs of implicit pitfalls. likewise, cautions frequently go unnoticed due to poor configuration or alert fatigue. To combat this, configure meaningful cautions and assign a devoted platoon or service to cover logs regularly. Use SIEM( Security Information and Event Management) tools for better visibility and briskly response times.
6. Allowing Broad Rules rather of Specific Bones
Using broad “ allow all ” or exorbitantly general rules makes it easier for bushwhackers to bypass your firewall. For illustration, allowing full access to an entire subnet rather of a specific IP or harborage greatly increases threat. also, it complicates troubleshooting and network performance tuning. rather, produce grainy rules grounded on stoner places, services, or operations. This minimizes access and ensures only what’s necessary is permitted.
Conclusion
Firewall security isn’t just about turning it on — it’s about managing it intelligently. From failing to modernize firmware to ignoring logs, these common miscalculations can be expensive. Thankfully, utmost of them are preventable with regular checkups, streamlined configurations, and smarter network segmentation. Eventually, by feting and addressing these crimes, you strengthen your defense, ameliorate network performance, and cover your digital means more effectively.



