The protection of privacy and data in the internet sphere is now a must in the digital world which is changing at a very fast pace. A lot of users use a VPN (Virtual Private Network) for their internet connections security, or a DPN (Decentralized Private Network) for the same purpose. They are so different in the way they function even though both are for the same purpose of data protection. Let’s see the features that are common, the distinctions, and what might be your perfect choice in 2026.
What Is a VPN?

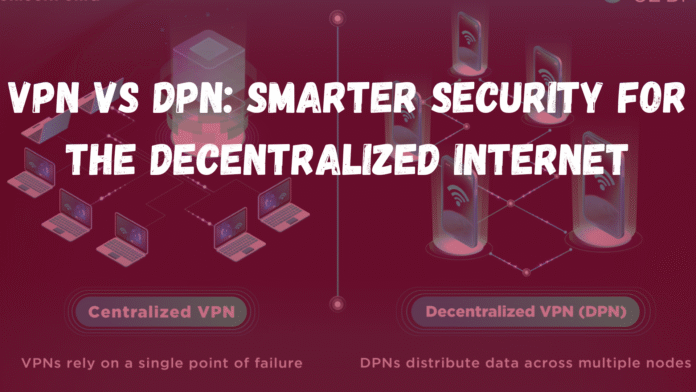
A VPN (Virtual Private Network) can be regarded as a tunnel that is private and is created between the device and the internet. The encryption of the connection is done along with the masking of the IP address. Thus hacking or spying ascendants will not be able to easily monitor your behavior.
Furthermore, people widely use VPNs for remote working, online watching, and private browsing. They fall under the category of centralized networks, which implies that the internet connection of the user goes through the VPN servers. This scenario places the user’s data security in the provider’s trust level.
What Is a DPN?
In comparison to the VPNs, DPNs are more of the privacy technology’s advanced version. One main difference between DPNs and VPNs is that the former do not work with a centralized server at all. The latter, however, uses either blockchain technology or peer-to-peer nodes to share and encrypt the traffic.
Additionally, they are more transparent in a way that no single company is deciding upon the data. Hence, no single company is controlling it. Already, the decentralized networks are gradually taking over the tech-savvy areas of crypto users.
Key Differences Between VPN and DPN
Although both technologies are meant to secure your internet connection, VPNs and DPNs choose different paths to achieve that goal.
To begin with, a VPN operates on a centralized model. The provider is responsible for managing the entire network of servers, applying the encryption, and setting the policies. DPN, on the other hand, a decentralized model distributes all these functions across various nodes.
Another difference is that while some VPNs might log user data. Most DPs are designed in a manner that there is no central logging at all. Lastly, DPNs are often backed by the use of blockchain technology, thereby increasing data integrity.
Similarities Between VPN and DPN
Privacy protection, tracking prevention, and secured communication are some of the common goals of both VPNs and DPNs. They implement strong encryption protocols, conceal your IP address, and protect online transactions.
In the same way, the two are indispensable not only for companies but also for individuals who frequently exchange confidential information. It does not matter if you are a remote worker, an online trader, or someone who wants to browse the internet anonymously; both tools will give you an important layer of protection against cyber threats.
Which One Should You Choose in 2026?
The VPN versus DPN debate boils down to personal preference. If you are after an uncomplicated, trustworthy, and affordable option, then go for a VPN. However, if you are looking for top-notch privacy protection, DPN is the smarter alternative.
Cybersecurity trends in 2026 indicate a significant movement towards decentralized networks. The widespread adoption of Web3, along with blockchain-based solutions, will make the DPNs not only more accessible, but also faster and more reliable than ever before.
Final Thoughts
In the comparative analysis of both VPNs and DPNs, strengths and weaknesses are their common grounds. Though VPNs are still around for hiding your digital presence and providing secure channels for the data, DPNs are here for total anonymity and the end of the line in privacy. So, what really matters is considering your daily online activities and the level of security necessary for you before making the choice.
When the clock strikes 2026, cyber threats would become more versatile and thus the only way to go is being constantly updated which will be your best defense. Make your way to Jazz Cyber Shield for trustworthy and up-to-date cybersecurity tools — 100% new and ready to defend your digital domain with precision and trust.



Really helpful read. The diagram comparing VPN and DPN routing made everything click instantly.
Really insightful article! I’ve used VPNs for ages, but I’d never heard much about DPNs until now. Looks like the future of private networking!
Absolutely brilliant explanation! I never really understood how DPNs differed from VPNs until now.
I like that you didn’t just hype DPNs — you showed where VPNs still make sense for most users.
Great explanation! I finally understand the key difference between VPN and DPN.
Brilliant explanation — especially the part about decentralization and node distribution. Made complex concepts easy to grasp.
This was a really clear and informative breakdown of VPN vs DPN. I liked how you explained decentralized networks in simple terms. The comparison helped me understand real-world use cases better. Great read for anyone exploring modern privacy tools. Keep up the good work!
Loved this! It’s nice to see a neutral take rather than someone pushing one over the other.
Your comparison table was very useful. I’m interested though — do DPNs have the same encryption standards as most VPN providers? That could make or break adoption rates.
This post helped me a lot. I never knew DPN worked so differently compared to a normal VPN!
I’ve been using a VPN for years, but after reading this I’m tempted to give a DPN a try. Great insights!
Great article! Didn’t realize that DPNs don’t rely on central servers. Seems like a huge privacy benefit.
I’ve read dozens of articles on this topic but this one actually made sense.
Clean and well-structured article. The comparison between VPN and DPN in a decentralized setup was explained really well. Helped me understand where each one actually fits.
I was confused about how DPNs differ from VPNs before reading this. Thanks for clearing that up with such a balanced comparison.
This blog does a great job explaining the differences and similarities between VPN and DPN in a very clear and natural way. I liked how the concept of decentralized networking is broken down into simple terms. The comparison helps readers understand when a traditional VPN works and when a DPN makes more sense. It also highlights privacy, security, and control in a balanced manner. The examples feel practical and easy to relate to real-world use. Overall, this article is a helpful guide for anyone exploring decentralized networks and online privacy.
Really well written. Loved how you compared both privacy models without devices.
Loved this post! The privacy and control aspects of DPNs sound fascinating — I might experiment with one for my home network.
Really insightful! I never realized how DPNs distribute traffic across multiple nodes—it seems like a smarter solution for privacy.
Really informative. The comparison table was especially clear and helpful!
Amazing article — easy to read, professional tone, and straight to the point.
Really enjoyed this article on VPN vs DPN. The explanation of decentralized networks was easy to follow and very practical. It cleared up a lot of confusion for me. Short, sharp, and useful content. Nicely done!
The analogy between VPN centralization and DPN peer distribution was spot-on. Made it so easy to understand.
I really enjoyed reading this article. It answered so many of my doubts about decentralized networks and privacy protection. The language was easy, the structure was perfect, and the information was truly helpful. Well done!
Superb breakdown! The contrast between centralized VPNs and decentralized DPNs was spot on. Very well explained.
Excellent breakdown! This really helped me understand VPNs versus DPNs.
Love how clearly everything is explained here. Keep posting more like this!
Simple yet deep! You explained decentralization so even a non-tech person like me could follow along.
Really enjoyed this article! I never fully understood the subtle differences between VPNs and DPNs before. The examples you used for decentralized networks made it super clear. Great read, looking forward to more posts like this!
Thanks for the clear comparison. Your explanation of encryption differences between VPNs and DPNs made everything much easier to understand.
Short but powerful explanation. I liked how you explained decentralization in simple steps.
Really clear and easy to follow. I appreciate how you highlighted the similarities and differences without getting too technical. Great job!
Fantastic article! I especially liked the section on decentralized networks. Jazz Cyber Shield always shares reliable and clear guidance.
Very helpful and easy to understand! I now know the key differences between VPN and DPN. Jazz Cyber Shield’s explanations make online security less intimidating. A must-read for anyone working remotely.
Great article! I learned a lot about the differences between VPNs and DPNs. The examples in decentralized networks really helped me understand why DPNs are more secure in certain scenarios.
I really enjoyed this blog! VPNs and DPNs were explained clearly and simply. Jazz Cyber Shield always delivers helpful cybersecurity guidance. I’m bookmarking this for future reference!
Loved this comparison. VPNs feel limiting now—DPN sounds like the future, especially in restricted regions.
Spot on about scalability! The part explaining how DPNs handle bandwidth distribution was particularly insightful.
Loved this! Clear, balanced and informative. I’ve bookmarked it for future reference.
It’s brilliant how you connected DPNs to blockchain concepts like consensus. That crossover was perfectly explained.
Interesting post! I didn’t realise DPNs could offer such privacy advantages over traditional VPNs. Thanks for breaking it down so clearly.
Great job! I liked how you touched on the limitations of both systems — not just the advantages. It felt like an honest take.
Good point about latency — that’s something most people forget when talking about decentralization.
Very helpful article. I appreciate that you discussed both performance and security trade-offs.
Honestly, this is one of the few blogs that made DPN easy to understand for beginners.
Excellent read! The comparison of VPN and DPN was very clear, and I now understand why DPNs are better for privacy-focused applications in decentralized networks.
Excellent breakdown of VPN vs DPN! I especially liked the decentralized network insights. Jazz Cyber Shield makes cybersecurity easy to understand. Very practical and useful information.
Fantastic article! The section comparing VPNs and DPNs in decentralized networks is very helpful. I especially liked the examples illustrating privacy benefits. Very clear and concise.
I’ve been exploring decentralized networks lately, and this blog came right on time.
Good job breaking this down. I think DPNs will gain traction as more people understand data ownership. VPNs still have a place, but decentralization feels more ethical.
I’m really intrigued by DPNs now. Do you think they’ll replace VPNs entirely in the next few years?
Brilliant piece. DPNs seem so promising, especially for those living under strict censorship.
Very informative article! Clear and concise explanations — much appreciated.
Very helpful article! The distinction between VPN and DPN is much clearer now. The examples in decentralized networks are particularly useful for understanding real-world applications
Great comparison! I appreciated how the article highlighted the privacy and security differences between VPNs and DPNs. The content is easy to follow and very practical for anyone in tech.
Interesting read. I’m curious though — how’s the latency on a DPN compared to a VPN?
Jazz Cyber Shield really knows how to simplify complex cybersecurity concepts.
Very helpful! I learned so much about decentralized networks and online security. Jazz Cyber Shield explains everything in a clear, simple way. I feel confident applying these tips immediately.
I’d never heard of DPNs before this. Sounds like they could be game-changers for privacy-focused users.
Great write-up. I like that you covered the pros and cons of both technologies instead of pushing one over the other.
I wish I found this blog earlier, it cleared up weeks of confusion about VPNs.
Excellent guide! I never realized how much privacy DPNs could offer compared to VPNs. The breakdown of how both work in decentralized networks is very helpful, and the real-world examples make the concepts easy to grasp. The writing is simple and digestible, even for beginners like me. I now understand the risks of open ports and misconfigured services and feel ready to experiment safely. The practical tips and step-by-step approach are perfect for anyone learning network security. I’ll definitely share this with my colleagues!
Really detailed and well written — this kind of info is hard to find online.
Loved the clear layout. It’s rare to find tech content that’s this easy to digest.
Thanks for clarifying the similarities as well as the differences. Encryption works differently than I thought!
Fantastic guide! Now I know when to use a VPN or a DPN in a decentralized network.
Really enjoyed this breakdown of VPNs vs DPNs! The comparison of how they handle decentralized networks was super clear. I didn’t realize DPNs could offer that extra layer of privacy. Definitely learned something new today!
Fantastic comparison. The way you contrasted DPN node validation with VPN server authentication really helped me visualize the difference.
Loved this article!
So DPNs basically remove the middleman that’s fascinating. Thanks for explaining it so plainly!
This was a really clear comparison. I always thought VPN and DPN were almost the same, but this article explained the differences in a simple way. The decentralized angle was especially interesting.
Really enjoyed this post! I’ve been trying to wrap my head around the differences between VPNs and DPNs for a while, especially when it comes to decentralized networks, and this article explained it so clearly. I liked how you didn’t just focus on the technical side but also talked about real-world use cases, like privacy, security, and network control. The comparison of how each handles data and anonymity really helped me see when a VPN is enough and when a DPN makes more sense. Honestly, I didn’t know much about DPNs before, and now I feel like I can make an informed choice depending on my needs. Appreciate the effort you put into breaking down such a complex topic without making it overwhelming!
Informative post. The diagrams showing how traffic flows through DPNs versus VPNs were particularly useful.
I really liked this article! The VPN vs DPN comparison was very clear. Jazz Cyber Shield consistently provides accurate and practical security advice. I feel more confident online now.
Very informative article! The comparison of VPN and DPN was easy to follow. Jazz Cyber Shield provides up-to-date advice for online safety.
Excellent breakdown! The article made it very easy to understand why DPNs are gaining importance in decentralized networks.
Great comparison! I finally understand how DPN differs from traditional VPN services. The security points were clear and practical.
Really useful post! Makes technical concepts easy to understand.
I really enjoyed reading this article! The comparison between VPN and DPN was clear and easy to understand. It’s great how you explained the benefits of decentralized networks in 2026. Thanks, Jazz Cyber Shield, for providing such useful insights — I feel more confident about securing my online activity now!
Your breakdown of latency differences was incredibly useful. I thought DPNs were always faster, but now I understand the real-world factors. Cheers for the clarity!
Informative piece. Highlighting performance differences was helpful; latency is always my main concern with VPNs.
Really appreciated the section comparing privacy levels. I didn’t realize DPNs can bypass central servers entirely.
This article is excellent! I especially appreciated the focus on privacy and security in decentralized networks. The explanations between VPN and DPN were clear and practical.
It’s refreshing to see someone address privacy without resorting to fear tactics. Your technical precision was impressive.
Great article! I now feel much more confident about working securely in decentralized networks.
This blog helped me understand decentralized networks much better. The VPN vs DPN comparison was detailed but easy to read. I liked how each concept was explained clearly. The article flows nicely without confusion. It’s both educational and interesting. Keep sharing such content.
Great read! The comparison between VPN and DPN is very clear.
Very clear and detailed! I now understand the key distinctions between VPN and DPN, particularly in decentralized networks.
Shared this with my entire cybersecurity Masters group at Edinburgh Uni. Everyone’s now debating whether to ditch their uni-provided Cisco AnyConnect for a DPN. You’ve started a revolution!
This blog was a fantastic breakdown of VPN vs DPN! As someone who works remotely across multiple countries, I’ve relied heavily on VPNs for years. I’ve recently been hearing about DPNs and how they tie into decentralized networks, but wasn’t sure how they really differed. This article cleared it all up—especially how DPNs offer more privacy by not relying on centralized servers. It’s exciting tech and the blog made it very digestible. Definitely opened my eyes to trying DPNs for added security.
Your diagram of data flow differences between VPN and DPN really helped me visualize what’s happening.
Interesting. I wonder how DPNs will scale if many users adopt them.
Loved this read! The section on security differences between VPNs and DPNs was super helpful. Definitely bookmarking this for future reference.
I found this article really insightful! It clearly explains the key differences between VPNs and DPNs, especially when working on decentralized networks. I didn’t realize how much control a DPN can give over data privacy compared to a traditional VPN. The examples were really helpful too. Definitely bookmarking this for future reference!
Very helpful! I’ve been deciding whether to switch for remote work. This cleared up a lot.
This is exactly the type of deep-dive content I look for. You made decentralization feel practical, not abstract.
Never thought I’d see DPNs explained so clearly. I’ll definitely share this with my tech group — very informative.
Very insightful post! I learned the differences between VPN and DPN and why decentralized networks matter. Jazz Cyber Shield provides clear and useful guidance. Highly recommend reading this!
Interesting read! I like how you highlighted both security and performance trade-offs.
Great angle on decentralization. DPNs seem more “internet-native” than VPNs.
Loved this! Makes it way easier to explain VPN vs DPN to colleagues.
This is a fantastic explanation of VPNs versus DPNs. The article is very clear and easy to understand, especially the part about decentralized networks.
You’ve done a great job simplifying something usually overcomplicated. The decentralized trust model part was brilliantly written.
Superb clarity! The pros-and-cons chart was especially useful for comparing connection reliability across VPN and DPN solutions.
Good article. The way DPNs distribute traffic across nodes makes a lot of sense for avoiding bottlenecks.
Good post! I’d love to see benchmarks comparing speed and reliability next time.
Your writing is so easy to follow even when the topic’s complex. Finally a blog that doesn’t treat readers like idiots.
This blog post is fantastic! VPN vs DPN comparisons were very clear, and the article covers everything I needed to know. Jazz Cyber Shield consistently provides reliable cybersecurity guidance.
This was one of the most practical technical blogs I’ve read recently. You’ve clearly worked in networking or cybersecurity.
Brilliant analysis! The graphics in your article also made the comparison much easier to follow.
Thanks for writing this — I’d been hearing about DPNs on Reddit and didn’t fully get the concept until now.
Fantastic post! The performance versus privacy trade-off you outlined between VPNs and DPNs was a real highlight.
Really informative post! It clearly explains the key differences between VPNs and DPNs. Learned a lot!
Appreciate the balanced view. Many articles oversell DPNs without mentioning their limitations.
Do you think DPNs will replace VPNs completely in a few years? Seems like where the web is headed.
Clear, modern, and well-structured. The decentralised network part was explained brilliantly. Keep these coming!
A brilliant exploration of decentralized governance! I like how you highlighted community-driven validation as a key advantage.
Great comparison! I’ve been thinking about switching from VPN to DPN, and this blog helped answer most of my questions. Much appreciated.
Very detailed and insightful. You managed to cover encryption, topology, and decentralization without losing focus.
Really clear explanation of decentralized privacy. Perfect for beginners like me.
I’ve read quite a few comparisons, but none went this deep into performance benchmarking. Really insightful!
Thanks for explaining the similarities too—lots of people forget both VPNs and DPNs encrypt traffic.
Excellent article. I hadn’t realized DPNs could improve resilience against server failures compared to traditional VPNs.
Really well-structured article! The comparison between VPN encryption tunnels and DPN’s distributed architecture was particularly enlightening.
Refreshing read. The diagrams explaining routing differences made it super easy to understand.
Finally someone who gets it! Been using Mysterium for 6 months and the speed in Birmingham is insane compared to NordVPN. Your latency table is spot-on. Thank you!
This article deserves more views. You explained decentralized networking better than most YouTubers! Very impressive work.
I liked how you explored governance in decentralized networks. That’s such an underrated but vital part of DPN success.
Fantastic post! I didn’t know much about DPNs before, but this article clarified everything. Jazz Cyber Shield provides excellent, easy-to-follow guidance. I feel more confident about securing my network now.
Great post! I now understand the similarities and differences between VPN and DPN. Jazz Cyber Shield consistently shares practical cybersecurity insights. A must-read for anyone online!
This article is so clear and well-written. Great resource for anyone working in decentralized networks.
Thanks for this comparison! I always thought VPNs and DPNs were basically the same. This post cleared up so many misconceptions for me. Great job!
I appreciate how you stayed objective. Too many articles push one side — this felt fair.
Very useful. The part about latency differences was particularly enlightening for real-time applications.
VPNs have been my go-to for years, but I might give DPNs a go now. Excellent insights!
Excellent write-up. The side-by-side comparison of VPN vs DPN is perfect for understanding when each is best. I learned a lot about decentralized networks.
This article is very helpful! I had some confusion about VPNs and DPNs, but the detailed explanations cleared everything up.
Loved the clarity in your explanations! You managed to make a fairly technical topic sound approachable. Would love to see a follow-up post on DPN use cases for remote workers.
This article cleared up so much. I liked the section comparing routing overhead and latency — very practical. I’m curious how DPN implementations handle large file transfers across many peers.
Great article! I work remotely and always wondered whether switching from a VPN to a DPN is worth it. Your pros and cons section answered all my questions. Nicely written and simple to follow.
This post breaks down VPNs and DPNs in a way that’s easy to follow. I liked the way it highlighted both differences and similarities. The explanations about decentralized networks were especially useful. Definitely informative!
Very helpful and detailed post! The illustrations of VPN vs DPN made it easy to grasp. I appreciate Jazz Cyber Shield’s clear explanations.
Fantastic post! I now clearly see the differences between VPN and DPN and how decentralized networks work. Jazz Cyber Shield provides really practical advice.
I found this blog very helpful! The explanations of VPN and DPN are simple and easy to understand. Jazz Cyber Shield provides trustworthy insights for online safety.
Excellent guide! I understand how VPNs differ from DPNs and the importance of decentralized networks. Jazz Cyber Shield is always reliable for cybersecurity insights.
Fantastic article! I now have a better understanding of VPNs and DPNs. Jazz Cyber Shield always explains cybersecurity in simple terms. Very helpful for personal and professional online safety.
Informative and easy to read! The article breaks down VPNs and DPNs in a way anyone can understand. Jazz Cyber Shield always shares reliable information. I feel much safer online now.
Super informative. I’d love to see a case study on how businesses could adopt DPNs safely.
Nicely done! The part about node distribution and trust models was particularly useful.
Great insights! I didn’t realize DPNs could be more resilient in case of node failures.
This article really helped me understand the key differences between VPN and DPN. I liked how the author explained things in a simple and clear way. The examples were very practical and easy to follow. Definitely a helpful read for anyone exploring decentralized networks.
Fantastic guide! The comparison between VPN and DPN was easy to follow. I especially liked the section on decentralized networks. It’s reassuring to know there are tools to protect our online privacy. Thanks, Jazz Cyber Shield, for such a practical article!
This is by far the best VPN vs DPN breakdown I’ve seen. The decentralized authentication concept was explained beautifully.
VPNs feel outdated after reading this. Thanks for the neat comparison.
Excellent article! The VPN vs DPN comparison is detailed and straightforward. Jazz Cyber Shield offers trustworthy information for securing digital activities. I feel more informed now.
Very informative and well structured. The examples made it so much easier to understand how DPNs handle traffic differently.
Informative and straight to the point.
Great post! I loved how the article explained decentralized networks and online privacy. Jazz Cyber Shield consistently shares trustworthy insights.
I appreciated the technical depth here — especially the part about node validation and connection routing in DPNs.
Very informative article! I appreciate how VPN and DPN differences were broken down. Jazz Cyber Shield always shares relevant, updated information. This is perfect for anyone wanting to stay secure online.
This blog post is excellent! I appreciate the detailed explanation of VPN and DPN. Jazz Cyber Shield always provides accurate and practical advice. Highly recommended for anyone concerned about online privacy.
Awesome explanation! I always got confused between VPN and DPN, but now it makes total sense. The decentralized part is really cool.
Loved the comparison! Makes choosing between VPN and DPN much easier.
Excellent read! I learned a lot about VPNs, DPNs, and decentralized networks. Jazz Cyber Shield explains cybersecurity concepts in a way that’s easy to follow. I feel more confident browsing online now.
Loved the explanation of node-to-node encryption in DPNs. So many people confuse it with regular VPN tunneling.
This post really helped me understand the nuances between VPNs and DPNs. The decentralized network examples made it easy to grasp the importance of privacy and security.
Fantastic article! I didn’t know DPNs used peer-to-peer connections for added privacy — that’s clever tech.
This is one of the most thorough articles I’ve read on VPNs and DPNs. I really appreciate how you broke down both technologies, not just in terms of security but also their role in decentralized networks. The examples you provided made complex concepts much easier to understand, especially the part about how DPNs differ in routing and privacy compared to traditional VPNs. I also found the comparison of speed and reliability very insightful. After reading this, I feel much more confident about choosing the right solution for my work and personal use. Excellent work on making such a technical topic accessible!
This article is very informative! I now clearly understand the key differences between VPN and DPN. Jazz Cyber Shield always provides reliable insights. I appreciate the simple explanations and examples — they make cybersecurity less intimidating. Definitely a must-read for anyone working online!
Well written and educational. I especially liked the practical examples you gave.
Very useful guide! The comparison charts and examples made it much easier to digest. I feel more confident in choosing the best solution for secure, decentralized work environments.
Great article!
Very clear and helpful article. I learned a lot about the differences between VPNs and DPNs. The section on decentralized networks made it easy to understand why DPNs are gaining popularity.
Loved how you compared privacy and security for both systems. Easy to read and understand.
Perfect comparison. I didn’t know DPNs distribute traffic differently from VPNs. Your diagrams and examples helped a lot. Keep posting more cybersecurity content!
Nice overview. I think both VPNs and DPNs have their place — one for ease, one for ideology. Great balance in your article.
This is such a helpful post! I never realized how much decentralized networks could impact VPN and DPN performance. The comparison table really helped me visualize the differences, and your writing style made everything easy to follow. I’ll definitely be recommending this article to friends who are trying to understand network privacy better.
Good mention of legal considerations too. Even decentralized systems can face regulatory challenges.
This article made VPN and DPN very easy to understand. Great work.
Great article! I now understand the difference between VPN and DPN and how each helps in decentralized networks.
Very helpful! I’ve been exploring decentralized networking tools lately and your explanation gave me a good starting point. Loved the comparisons.
Interesting concept! But are DPNs fast enough yet for video streaming and gaming?
Your take on DPN scalability was particularly insightful. It’s impressive how you balanced technical depth with readability.
This article offers a clear and well-structured comparison between VPN and DPN. I liked how the decentralized network concept was explained in simple terms. The privacy discussion was especially helpful. It didn’t feel overloaded with technical jargon. The flow of information was smooth and easy to follow. A very informative and enjoyable read.
love your blogs
Fantastic read!
Brilliant post! The way you explained the security and performance aspects of VPN vs DPN was really useful. I feel more confident now in choosing the right solution for our company’s remote network setup.”
Fantastic article — easy to follow, informative, and well structured.
Clearest comparison I’ve seen so far. Appreciate your writing style—it’s easy to follow.
This blog clearly explains how VPN and DPN work in modern networks. The comparison felt fair and easy to understand. I appreciated the focus on privacy and decentralization. The content is informative without being boring. It’s suitable for both beginners and tech users. A well-written post.
Great deep dive!
Great article! I liked how you highlighted both the similarities and key differences between VPNs and DPNs. It definitely helped me understand how decentralized networks change the game.
The explanation of decentralized networks in this article is very impressive. I liked how VPN and DPN were compared in a practical way. The language is simple and reader-friendly. It’s great for anyone interested in online privacy. The structure of the article is neat and clear. Very useful information.
Your comparison between VPN and DPN is absolutely brilliant. I liked how you explained the similarities and then highlighted where each one works best. This kind of deep yet easy content is very rare online. Keep posting such valuable tech knowledge.
Excellent write-up!
VPNs are convenient, but DPNs might be the real step forward for Web3 users. Nicely presented!
This is the most balanced and technically sound VPN vs DPN breakdown I’ve read. Your research clearly shows!
Loved the clarity and examples. I’ll share this with friends who ask about VPNs and DPNs.
Very informative article! I liked the focus on decentralized networks and security tools. Jazz Cyber Shield makes complex topics easy to understand. I now feel more prepared to protect my online activity.
This guide is excellent! I liked how you explained both the similarities and differences between VPN and DPN in a decentralized setup. The examples were practical, and the language was easy to follow. It’s rare to find content that’s detailed yet simple, and I really learned a lot. Thanks for sharing this!
Great comparison! I didn’t realise how DPNs reduce single points of failure compared to VPNs. The real-world examples made it easy to understand. Keep posting content like this.
I found this article very helpful in understanding decentralized networking. The differences between VPN and DPN were explained clearly. The writing style is simple and engaging. It helped clear many doubts I had before. The examples made the content relatable. Overall, a great read.
A proper educational read! You covered security, performance and architecture all in one place. Perfect for beginners and techies alike.
Great read! I liked the comparison chart—it really highlighted the differences and similarities. Now I know when to use a DPN over a VPN for better security.
This was super helpful! I always get confused between VPNs and DPNs, but the way this post breaks it down makes it easy to understand. The focus on decentralized networks was a nice touch!
I really enjoyed reading this post. It breaks down VPNs and DPNs in a very simple and understandable way. The examples and comparisons were especially helpful. I feel much more confident about using these networks after reading this.
This article helped me understand the real differences between VPN and DPN. I was always confused about which one to use for secure work. Thanks for the clear explanations!
Loved this post! The VPN vs DPN comparison is clear and practical. Jazz Cyber Shield provides very useful tips for online safety.
http://okna-plastic-8.ru/ – пластиковые окна Москва с выездом бесплатный замер консультация специалиста выезд в день обращения
Brilliant comparison! The decentralized network examples really helped me get the concept.
Great article. I wasn’t aware of some of the similarities between VPN and DPN—really useful.
Very clear explanation. I didn’t know DPN worked this way. Helpful article.
Clear and concise. I now understand why DPNs are gaining traction in crypto networks.
This post gave me a much better understanding of decentralized routing and encryption redundancy. Keep writing more like this!
Balanced write-up. It’s helpful that you didn’t just declare one better than the other.
The comparison chart was my favourite bit — simple, direct, and informative.
Thank you for this deep dive! I was always confused by DPN terminology, but you broke it down really well.
Great article — you explained decentralization in such simple terms. I finally get it!
This article really helped me understand the difference between VPNs and DPNs. I liked how you explained decentralized networks in a simple way. Great read!
Your comparison tables are pure gold.
Excellent post! You broke down complex architecture principles in a way that’s easy to grasp but still technically accurate.
Really insightful comparison! I never realized how DPNs could offer more privacy in decentralized networks than traditional VPNs. Great examples and clear explanation.
The similarities part was very interesting. I learned something new.
Your writing makes a complex subject sound simple. Kudos!
Helpful and very easy to understand. Keep sharing more tech content.
I found this blog very helpful and easy to read, especially the explanation of how DPN works in a decentralized environment. The comparison with VPN was clear and practical. The writing style is smooth and beginner-friendly. It’s great for anyone trying to learn about online privacy and network security. The article feels well-researched and organized. I really enjoyed reading it.
Thanks for this! The “real-world use cases” section was incredibly valuable. Helped me see when a VPN is still the better choice. Great work!
Really informative! I’ve been using VPNs for years but had no idea about DPNs. Your breakdown of decentralized routing is super clear.
The section on latency and network efficiency really stood out. You managed to cover both performance and privacy angles elegantly.
Excellent insights. I appreciate how you explained the peer-to-peer model of DPNs — it cleared up a lot of confusion about decentralized routing.
Good stuff! I’d love to see benchmarks comparing connection speeds between VPNs and DPNs.
I appreciate how you compared security models in detail. Most people just assume VPNs are the gold standard, but DPNs seem to be catching up fast!
This blog really helped me understand the difference between VPN and DPN in a clear and simple way. The examples were practical and the explanations were detailed without being confusing. I genuinely learned something useful from this post. Great job!
This article is very useful! I now understand how DPNs differ from VPNs and their benefits. Jazz Cyber Shield consistently provides practical and updated cybersecurity guidance.
This article makes me want to switch from my VPN provider to a DPN service. Great job!
Great comparison! I like how you broke down the differences in security and control. Makes it easier to choose between a VPN and a DPN for daily use.
Very insightful! I appreciate the detailed explanation of how DPNs differ from traditional VPNs.
Excellent comparison! I especially liked the real-world examples.
This was super helpful. I didn’t realize DPNs work without a central server, which really increases privacy. Very informative for beginners like me!
This post does a great job breaking down VPN versus DPN in a decentralized network setup. I especially liked the focus on transparency, trust, and data routing. The content feels well-researched and written in a way that both beginners and tech-savvy readers can enjoy. It’s informative, relevant, and easy to follow from start to finish.
I’d never even heard of DPNs before. Thanks for introducing me to the idea.
I’ve read a few articles on VPNs and DPNs, but this one is by far the clearest. It breaks down complex concepts without making it confusing. I especially liked the section on decentralized networks. Great work!
I really enjoyed reading this blog as it breaks down VPN and DPN very nicely. The similarities and differences were explained clearly. The decentralized aspect was easy to understand. This article is perfect for beginners. The tone is friendly and informative. Great work overall.
The section on resilience in decentralized networks stood out to me. Very insightful.
Really enjoyed this read. Your point about latency differences was eye-opening—definitely something to consider for real-time applications.
This was a solid and easy-to-follow comparison of VPN and DPN. The decentralized angle was explained really well. Quick read but very informative. Nice work!
Great article! The similarities section was especially useful. Didn’t realise how different the trust models were until now.
This is an amazing guide! I appreciate how VPN and DPN were compared in a simple way. Jazz Cyber Shield always shares up-to-date information on cybersecurity. I’ll definitely share this with my colleagues.
I liked how you kept it unbiased. Both technologies clearly have their place.
Helpful breakdown of encryption differences. One suggestion — maybe add a short checklist for choosing between VPN and DPN for small businesses.
Very clear explanation. I’ve used VPNs for years; now I understand scenarios where DPNs truly shine, especially for censorship-resistant communication.
Fantastic explanation! I now understand the differences between VPNs and DPNs and their applications in decentralized networks. Very insightful and easy to follow.
I liked how you connected both technologies with decentralized networks instead of treating them separately. The privacy comparison was especially helpful for understanding real-world use cases. Many blogs oversimplify this topic, but your explanation felt balanced and honest. The structure made it easy to follow from start to finish. It’s a great resource for both beginners and tech-savvy readers. Looking forward to more content like this.
Helpful comparison. Now I understand why VPNs are still relevant despite the advantages of DPNs.
Great article! I always thought VPN was the only secure option, but your explanation of DPN in decentralized networks really opened my eyes. Clear, simple, and very helpful!
Mate, this article is a lifesaver. I needed something to explain DPN tech to my team and this post nailed it. Excellent job — keep these coming!
Informative post! I now see why VPNs are still widely used despite the rise of DPNs.
Really informative! I hadn’t considered using a DPN for extra anonymity. Your explanation makes it easier to understand why decentralized networks are important.
Fantastic analysis. You touched on governance and community control within DPNs, which most blogs completely ignore.
I always wondered how DPNs handle traffic distribution. Your explanation made it so much easier.
I learned a lot from this article about VPNs and DPNs. The points were clear, and the examples made the technical concepts simple. I especially liked the section on decentralized networks. A great guide for anyone learning about networking.
Great read! I’ve been hearing about DPNs but didn’t quite understand how they work until now. Nicely explained.
Loved the explanation of routing mechanisms. Made the technical differences easy to understand.
Super clear comparison! This really helped me understand when to use VPNs and when DPNs make more sense.
This was a helpful comparison. I didn’t realise DPNs offer better anonymity in some cases. The examples you used made it easy to understand. Looking forward to more network-security articles!
This might be the best DPN vs VPN article I’ve read so far. You explained everything from privacy to bandwidth sharing. Brilliant work — keep posting more!
This blog cleared so many doubts! VPN is great, but the way you explained DPN for decentralized environments is impressive. Easy to read and very informative 👍
The way this article breaks down VPN and DPN is impressive and easy to follow. I appreciated the clear explanation of privacy and security benefits. The comparison felt fair and unbiased. Everything was written in simple language, which makes it accessible. The structure of the blog is clean and logical. This was a very useful read.
I enjoyed reading this post because it explains VPN and DPN in simple terms. The points are clear, and the examples really help. I also liked the part about working in decentralized networks. It’s a great guide for beginners and pros alike.
Really informative article! I’ve always used VPNs but never understood how DPNs work in decentralized systems. This blog cleared it up perfectly.
I really enjoyed this post! It clearly explains how VPNs and DPNs operate differently. The real-world examples of decentralized networks were particularly helpful.
This blog cleared all my confusion about VPN and DPN. Very informative and well written.
Excellent post!
This post explained VPN vs DPN in a very simple way. I finally understand how decentralized networks work.
Informative and clear! The VPN vs DPN comparison is detailed yet simple. Jazz Cyber Shield provides excellent cybersecurity advice.
Your blog helped me finally understand how DPNs mitigate centralized bottlenecks. Great mix of theory and practicality.
Really well-written piece. The explanation of how DPNs distribute traffic compared to traditional VPN servers was clear and easy to follow. Good balance between technical and readable.
Super helpful! The examples really helped me understand the practical use of VPNs and DPNs.
This article is excellent! The VPN vs DPN comparison is clear and detailed. Jazz Cyber Shield always shares accurate and practical cybersecurity tips. I feel much safer online after reading this.
Outstanding blog! It’s rare to find such a solid technical comparison written in plain, readable language.
This post does a great job explaining complex networking concepts simply. The VPN vs DPN comparison was clear and unbiased. I found the security section very informative. Everything was explained step by step. The article kept my attention throughout. Looking forward to more content like this.
Great read. I liked how you explained the privacy and control aspects without making it too technical. This helped me understand why DPNs are becoming popular.
This is one of the best articles I’ve read on VPN vs DPN. You not only explained the technology but also made it relatable with real‑world applications. Anyone interested in cybersecurity should read this blog. Excellent content!
This is a solid and informative post on VPN vs DPN that explains the similarities and differences really well. I liked how the article focused on real-world usage rather than just theory. The decentralized network concept was explained in a simple manner. The content didn’t feel overwhelming at any point. It’s a great read for both beginners and tech enthusiasts. Keep up the good work.
So well written! You highlighted the privacy benefits of DPNs without exaggerating them. Refreshing to read a balanced perspective. Subscribed!
This blog gave me a much clearer understanding of decentralized networks and how DPN differs from traditional VPNs. The points were explained step by step, which made it easy to follow. I liked the balance between technical details and simple explanations. The article is informative without being boring. It’s perfect for readers who want to learn something new. Really well done.
Very insightful article! I’ve been trying to figure out whether to use a VPN or DPN for my home office, and this explanation made it much clearer. Keep up the great work!
Brilliant guide!
Bloody useful read before Black Friday VPN deals hit! Saved me from renewing ExpressVPN. Just set up a Sentinel dVPN node instead and earning a bit of crypto on the side. Legend.
Brilliantly written! The pros and cons table made the comparison super easy to understand.
Really enjoyed this blog post — it breaks down complex concepts in a way that’s both engaging and highly understandable. The discussion on strengths and limitations of VPNs versus DPNs was particularly insightful. This guide is a valuable resource for anyone looking to protect their privacy in decentralized environments.
I found this article really helpful in understanding VPN and DPN. The comparison is clear, and the examples make it easy to see how each works. I also liked the tips on decentralized networks. Great read for anyone starting with network security.
Nice and concise explanation of VPN vs DPN. The way you connected it to decentralized networks made it really engaging and easy to grasp. Keep up the good work!
Good comparison! Nice that you didn’t oversell either tech and explained both strengths and weaknesses.
Really liked how this article breaks down VPN vs DPN in a simple way. The explanation of decentralization was clear and helpful, especially for readers new to privacy tech. Nice work!
very informative article.
This post explains the technical side without overwhelming the reader. Really appreciated the simple diagrams and examples. Great job!
This article gives a clear understanding of VPN and DPN technologies. The comparison was logical and well-presented. I appreciated the focus on decentralization benefits. The content is suitable for readers at all levels. Everything was explained clearly. Very well written.
I love how simple and clear this article is. The differences in data handling between VPNs and DPNs really stood out. Thanks for sharing this!
Short, sharp, and informative. The comparison between VPN and DPN was explained really clearly without overcomplicating it.
I liked how you explained consensus mechanisms within DPNs — it shows the maturity of decentralised network design.
Really enjoyed this article! The explanation of how VPNs and DPNs work in decentralized networks was very clear. I now understand the security and privacy advantages of each. Very helpful for anyone working remotely.
Super helpful! I always mixed up VPNs and DPNs, but the decentralized network section cleared things up.
Really insightful read. The similarities and differences are well explained—I now know when to use a DPN over a VPN.
Cracking article, lads. The bit about no single point of failure sold me. Just migrated my remote dev team from Surfshark to Sentinel dVPN. Zero regrets so far.
Well-researched and very readable. I’m sharing this with my classmates!
This article explains the difference between VPN and DPN in a very clear and simple way, making it easy for readers to understand decentralized networks. I really liked how both technologies were compared without making the content confusing or too technical. The privacy and security aspects were explained nicely with good balance. It helped clear a lot of common misunderstandings. The flow of the article kept me engaged from start to finish. Overall, this is a well-written and informative blog.
You did a wonderful job simplifying a complicated topic. DPNs sound like the logical next step for secure internet access.
Good read. The visuals showing traffic flow differences were particularly helpful.
I found this article very insightful. The explanation of how VPNs differ from DPNs was clear and concise. I like that Jazz Cyber Shield focuses on practical security advice.
Excellent comparison! I especially liked how you explained the role of DPNs in decentralized networks. Makes choosing between them much easier.
The point about trust in central servers really stood out. DPNs might be the next big step in privacy.
Absolute legend.
Fantastic guide! I especially liked the part comparing speed, encryption, and usability. Your insights make it much easier to decide which network solution fits different scenarios. Great post!
I appreciate how you tied user-centric design to decentralized privacy. It’s a modern, well-researched perspective.
Such a clear and refreshing read. The way you compared data privacy on VPNs vs DPNs genuinely helped me decide which one to use for remote work. Thanks for simplifying a complex topic!
Helpful comparison. Security-conscious users will appreciate your analysis of encryption techniques.
I enjoyed your explanation of how decentralization enhances trust through transparency. That’s the missing piece most people overlook.
As a privacy nut living in Glasgow, this is the clearest explanation I’ve read all year. The “centralised vs decentralised trust model” diagram deserves a medal.
Your explanation of decentralized privacy networking was outstanding. I learned many new things and now I finally understand the difference between VPN and DPN clearly. Thanks for sharing such quality information.
An impressive post. The way you covered the economic and technical layers of DPNs shows real understanding of the ecosystem.
Thanks for this. I work remotely and have been testing DPNs—your article confirmed a few suspicions I had.
Brilliant breakdown of VPN vs DPN — especially in the context of decentralised networks. Most articles focus only on privacy, but you’ve clearly explained performance and scalability differences as well. I’ve been testing both models for remote work, and the way you’ve compared latency, trust, and routing really helped me understand when each approach is more suitable. Keep publishing this kind of clarity — it’s rare to find.
I liked how you explained both security and performance aspects for VPNs and DPNs. The practical examples for decentralized networks really helped me understand which option fits best. Very insightful!
I had always been confused about the differences between VPN and DPN, especially in decentralized networks. Your explanation made it so clear, and the examples you gave were easy to understand. I now feel more confident about which one to use for my own setup. Keep up the great work, and I’m looking forward to more guides like this!
I love how clearly you explained the difference. Really helpful.
Super helpful! Excited about the future of decentralized networking thanks to your explanation.
Very informative and well‑researched blog. I appreciate how clearly you explained the technical terms and made them understandable for normal readers. This kind of educational content really builds trust. Keep it up!
VPNs feel outdated after learning about DPNs. Thanks for laying everything out so neatly.
Bloody brilliant write-up! Been paying Proton £8/month for years and never realised DPNs existed. Just installed Tachyon and my speeds in Cardiff actually went UP. Thank you!
Brilliant breakdown! I like how you compared both technologies without being too technical. VPNs feel outdated after reading this.
Very insightful post! I always had trouble understanding why VPNs and DPNs behave differently in decentralized networks, but your explanations clarified everything. I also appreciate how you highlighted their practical uses and limitations. This will definitely help me make better decisions when setting up my home network.
Loved this article! Clear, concise, and very helpful for someone new to decentralized networks. Thanks for sharing.
The part about peer-to-peer connections in DPNs was eye-opening. Makes sense why privacy is higher.
Your content always hits the right level of technical depth without overwhelming the reader. Top notch!
Top-notch article! I’ve always wondered how secure decentralized networks really are.
Loved the breakdown! You explained the pros and cons of VPN and DPN very clearly. It really helped me understand which one fits modern remote work setups better. Brilliant content!
This should be required reading before anyone buys another yearly VPN plan. The similarity/difference table is going straight into my Notion knowledge base.
Loved how you compared node distribution in DPNs with VPN server models. Very educational!
Clear and concise. I had no idea DPNs could actually reward users for sharing bandwidth. That’s such a clever concept!
I’m still not sure if DPNs can match VPNs for reliability. Would love to see some performance benchmarks!
Brilliant post! I’m especially impressed by how you linked decentralized consensus models to privacy assurance.
Bristol-based freelancer here. Been burned by VPN logs twice. Your section on “no logs by design” with blockchain verification finally convinced me to make the switch.
A very balanced article! You didn’t just hype DPNs but showed where each technology fits best. I shared this with my cybersecurity class. Thanks for the knowledge!
This article made me rethink VPNs. DPNs are more resilient, especially for censorship-heavy countries.
Good article. I liked the section on privacy implications—it made me reconsider how I connect to public networks.
Interesting perspective. I hadn’t thought about decentralization as a way to increase fault tolerance.
Loved this! The decentralized network explanation was spot-on. Most blogs make it too technical, but you kept it clear and practical. Thanks for the insight.
Really enjoyed this breakdown! I’ve used VPNs for years, but DPNs still felt confusing until now. Your explanation made the differences super clear, especially how decentralized nodes work. Great read!
Spot on! I’m experimenting with a few DPNs now and your pros and cons list matches my experience.
Loved this write-up! The pros and cons table was clear and helped me understand how DPNs outperform VPNs in resilience.
I found your explanation of how VPNs and DPNs work in decentralized networks very clear. The comparison chart was particularly helpful in summarizing key differences. Very useful for IT professionals and beginners alike.
Interesting point on latency differences. It really explains why DPNs might feel slower at first.
Amazing blog! The topic was complex but you handled it in a very smooth and reader‑friendly way. I especially liked how you discussed both advantages and limitations honestly. This is truly valuable tech content.
Excellent content as always. The examples of how DPNs handle censorship were really eye-opening.
Such a good read! You made a tech-heavy topic feel chill and easy.
Nottingham gamer here — the bit about DPNs dodging ISP throttling during peak hours is spot on. Switched to Mysterium last night and Warzone pingily feels smoother. You’ve got a new regular reader.
You explained complex topics like bandwidth sharing and node reliability so well. Very polished work.
Great detail on the authentication mechanisms within DPN frameworks. It’s that level of depth that sets your blog apart.
Top-tier explanation! You made DPN tech feel much more practical. Most blogs just hype it up, but yours actually teaches something.
This was a great read. I liked how you highlighted both similarities and real differences instead of overhyping one side. Very balanced and informative.
This blog made the comparison between VPN and DPN so easy to understand. The author explained the similarities and differences perfectly. I feel much more confident about choosing the right network solution now. Very informative!
This was such a clear read! The pros and cons list helped me see differences I never even considered. Sharing this with friends for sure.
Great comparison! I didn’t realize how DPNs differ from VPNs in a decentralized setup. Very useful for anyone working remotely or in crypto networks.
Really enjoyed this! The VPN vs DPN explanation was simple and straight to the point.
Fantastic write-up! I appreciated how you emphasized the shift from centralized authority to distributed control in DPNs.
Well-structured article! I think DPNs are the natural evolution of VPNs, especially as people seek more transparent digital tools. Great job summarizing the pros and cons.
Really informative post!
Excellent article! I finally understand the difference between VPNs and DPNs and how they affect decentralized networks. Your examples made it really simple to grasp. This will help me choose the right setup for secure remote work.
Very informative! I love how you compared VPN and DPN side by side. Makes choosing the right one so much easier.
This is an excellent and comprehensive article! I found the comparison between VPN and DPN really clear and easy to follow, even as a relative beginner. The real‑world examples and explanations of how each works in a decentralized network were particularly helpful. A very informative read for anyone interested in modern online privacy and network security.
Really interesting concept. I use a VPN daily, but the decentralized model of DPNs definitely sounds more secure in theory.
Excellent writing! The technical comparison of latency and bandwidth allocation was especially insightful.
Very well written. Loved the examples showing how traffic is routed differently in both systems.
Amazing breakdown of both networks. Please write more content like this.
This article gives a clear and balanced comparison of VPNs and DPNs while working in a decentralized network. I liked how the blog explained security, anonymity, and control without making it complicated. The writing feels smooth and informative, making it easy for readers to understand why decentralized solutions are becoming more popular. Really well written and insightful content.
Great post! The examples really helped me understand how DPNs work differently from VPNs in decentralized networks. Keep it up!
A thorough and enjoyable read! I especially liked the section explaining hybrid VPN-DPN interoperability.
Excellent explanation of decentralized routing! Your breakdown of how DPNs distribute trust among nodes was spot on.
Very insightful read! The part about how DPNs route traffic through multiple nodes really helped me understand why privacy improves. Clear and well-written.
Solid comparison between VPN and DPN. I liked how clearly you explained the decentralized angle — made the differences click instantly.
Wow, this is exactly what I needed! I always get confused with VPNs and DPNs, but your breakdown was simple and clear. I especially liked the section about real-world performance in decentralized networks. The post is both informative and easy to read, and it’s helped me decide which solution to choose for my devices.
Very clear and helpful article! The distinctions between VPNs and DPNs were well explained, especially regarding privacy and decentralized networks.
Really enjoyed this breakdown! I didn’t realize how differently VPNs and DPNs handle decentralized networks. The comparison was clear and easy to follow. Definitely bookmarking this for future reference!
VPNs still feel more user-friendly for now, but DPNs might catch up soon.
Very well-explained! I appreciate how the similarities were highlighted along with the differences.
I really liked how this article explained complex topics in a simple way. The differences between VPN and DPN were easy to grasp. The decentralized network explanation was very clear. The tone is friendly and informative. It kept me engaged till the end. A great blog post.
Love how detailed yet simple your explanations are. The part about decentralized networks and DPN security features was especially helpful. Thanks!
Helpful breakdown. I always thought VPNs were the only option. Now I see DPNs have a place too.
VPNs are great, but decentralization seems more sustainable long-term. Nice perspective!
Nice write-up! The part about speed vs security in DPNs was eye-opening.
Super interesting! I didn’t know DPNs could offer better censorship resistance than VPNs.
Super helpful for anyone working remotely. You highlighted the exact situations where VPNs still outperform DPNs. Great balance!
Loved the clarity here! VPN vs DPN is something I’ve been curious about, and this explains it perfectly.
The section on latency and network efficiency really stood out. You managed to cover both performance and privacy angles elegantly.
Your explanation about trust models was spot-on. VPNs rely heavily on providers, but DPNs remove that dependency — that’s huge.
Your comparison between VPNs and DPNs was very clear and insightful. I especially appreciated how you explained their relevance in decentralized networks — it helped me understand which solution fits best for different scenarios.
Thanks for explaining encryption differences. Node-to-node vs server-to-server is clearer now.
I wonder how regulators will deal with DPNs, considering there’s no central authority. You’ve got me thinking!
Very clear and balanced. The similarity section was helpful too, showing that both VPNs and DPNs encrypt traffic, just in different ways.
Super clean breakdown! VPN vs DPN finally makes sense. Love the way you explained it.
Really enjoyed this post! I always thought VPNs and DPNs were pretty much the same, but your explanation of how DPNs work in decentralized networks cleared things up for me. The examples were super clear and easy to follow. Definitely bookmarking this for future reference!
Really appreciated the clarity in your explanations. The part about node-to-node encryption in DPNs was especially helpful.
Great comparison! You explained the role of node distribution in DPNs so well. It’s fascinating how decentralization reduces single points of failure.
Loved how you broke down encryption layers between the two systems. That’s often skipped over in similar write-ups.
The way you update every article when prices drop or new firmware lands is unreal. Most sites just leave old info up. Respect.
Brilliantly written! The analogy you used for centralized vs decentralized connections made it click instantly.
This is a fantastic overview! Perfect for both beginners and tech enthusiasts.
Great work! You explained how decentralized routing impacts privacy and performance without oversimplifying.
Loved this article! It’s clear you put a lot of thought into explaining VPNs and DPNs in decentralized networks. The way you structured the post makes it easy to digest, and the examples made the concepts very relatable. I feel like I have a much better understanding now, and I’m excited to apply this knowledge.
Great breakdown between centralized and decentralized systems.
Great article! I hadn’t realized that decentralized networks could reduce single points of failure compared to traditional VPNs.
Fantastic post. I particularly liked your note on user control in DPNs — that’s something VPNs lack entirely. Looking forward to your next tech analysis.
This is the first time I fully understood decentralized networks. Thank you.
Really clear explanation of the differences between VPN and DPN! Helped me understand how each works in decentralized networks. Appreciate the examples and simple breakdown.
Quick, simple, and informative. Perfect comparison.
The article’s depth impressed me. It’s not easy to explain these technologies clearly, but you’ve nailed it.
Spot on! VPNs are great for now, but DPNs represent the evolution of internet privacy. Excellent perspective.
I’ve read several VPN vs DPN blogs, but yours nailed the technical distinction. The real-world examples helped a lot.
It’s practical and easy to follow — perfect for anyone setting up a decentralized network.
This is one of the most understandable guides I’ve seen on VPN vs DPN. The author made the differences clear without overcomplicating anything. I also appreciated the practical insights about decentralized networks. Very useful content!
Great insights! I’d like a follow-up comparing DPN security risks vs VPNs in more depth.
This blog was really easy to read and understand. I liked how it clearly outlined the pros and cons of VPN and DPN. The part about working in decentralized networks was particularly insightful. A very useful resource!
I’d never heard of DPNs before. This was an eye-opener — definitely something worth exploring.
Very informative. Your comparison of speed and security trade-offs will help me decide which tool to use for remote work.
Very helpful and clearly written. Would love to see a visual flow diagram next time!
I appreciate how you touched on decentralization from a privacy and performance perspective. Most blogs only mention one side. Nicely written!
Exceptional work — you’ve shown how DPNs can complement rather than replace VPNs. Balanced and future-oriented perspective!
Great article. You’ve made me rethink how I approach online privacy tools entirely.
I had no idea DPNs can dynamically reroute traffic. That seems like a huge advantage for reliability.
Brilliantly done! Loved your point about decentralization removing single points of failure.
Super insightful! I appreciate how you showed both strengths and weaknesses without favouring one side.
Loved your section about encryption layers. It’s refreshing to see a piece that compares VPN protocols with DPN’s blockchain-based security.
Very clear and informative. The security comparison section between centralized VPN servers and distributed DPN nodes was perfectly written.
Your tone struck the perfect balance between informative and accessible. I’m excited to see how DPNs evolve next.
One of the best blogs I have read on VPN vs DPN. Short and to the point.
This was a really smooth read. Simple explanations without dumbing things down. Helped me understand when a DPN actually makes sense.
This was such a clear and fair breakdown. Thanks for making tech easy to follow!
The pros and cons sections were especially helpful. Great work!
This answered literally every question I had before jumping into Web3 stuff. The “Similarities” table was gold. Subscribed and shared with my uni mates doing blockchain research in Manchester!
Interesting read! I always thought VPNs and DPNs were pretty much the same, but this blog clarified the key differences really well.
This blog is actually fire 🔥 Really helped me understand decentralized networks. Subscribed!
The real-world implications you mentioned — especially regarding censorship resistance — were thought-provoking.
Really well-structured article! The comparison between VPN encryption tunnels and DPN’s distributed architecture was particularly enlightening.
Outstanding piece! The part about decentralized bandwidth allocation and user incentives was my favourite.
Informative and concise. Really liked the focus on how each works in decentralized networks.
Loved the examples of DPN use cases. It gave me a much better idea of when to use one.
Loved this! Your comparison of centralized vs decentralized routing was spot-on. Helped me understand when a DPN actually performs better. Great read!
Very well written. Would love to see some benchmarks comparing speed and latency between VPN and DPN networks.
Nicely done. I’m curious about how DPNs handle speed compared to traditional VPNs.
This blog clearly explains the differences and similarities between VPN and DPN in a decentralized network. I really liked how the comparison focused on privacy, control, and performance in real-world use. The explanation felt modern, easy to understand, and useful for anyone exploring decentralized networking in 2026. Great content that adds real value to the topic and keeps the reader engaged throughout.
Great job! The difference between centralized and decentralized nodes was explained perfectly.
Clear and engaging writing! The diagrams made the differences between centralized VPNs and distributed DPNs instantly understandable.
I liked the neutral approach. Both VPNs and DPNs have strengths, and your article explains when each is more appropriate.
Your article helped me understand why someone would choose a DPN over a VPN in certain scenarios. The step-by-step explanations and examples were clear and concise.
Fantastic read. The performance and privacy pros/cons section was my favorite.
I appreciate the balanced tone — pro-DPN but without dismissing VPNs entirely. Very professional analysis.
Loved reading this! The decentralized nature makes DPNs seem far more future-proof. Brilliantly put.
Loved the bit about node diversity and security redundancy. That’s the kind of network-level resilience we need more of.
Nicely done. I think DPNs could become mainstream once they sort out speed and stability issues.
This is a solid and informative article on VPN vs DPN. The decentralized network explanation was especially useful. I liked how the content avoided unnecessary technical complexity. Everything felt well-organized and clear. The blog is easy to follow from start to end. Nicely done.
Really appreciated the neutrality. You made it easy to see when to use VPN vs DPN depending on the use case.
Loved it! I’ll definitely explore some DPN services now. Any recommendations?
Brilliant explanation! I’ve always been confused between VPNs and DPNs, but your breakdown made everything finally click. Clear, simple and super informative.
Brilliant article. The part about resilience in decentralized networks really stood out.
I like how you mentioned legal considerations too. People often forget decentralized systems can still face regulatory challenges.
I appreciate that you mentioned performance differences too, not just privacy aspects.
I never realized decentralization could apply to networking like this. Thanks for enlightening me!
I liked that you included potential drawbacks of DPNs—helps make a more informed choice.
Loved the structure of the article. Easy to follow even for someone who’s not super technical.
The scalability discussion was top-notch. You’ve highlighted why DPNs are likely to perform better under distributed loads.
Strong piece! The part about removing central trust anchors hit home. DPNs really are the future of secure connectivity.
Your diagrams made complex network routing feel approachable. Love the balanced tone — clearly written for people who actually understand networking.
Really clear explanation! This helped me understand VPNs and DPNs much better.
Loved how you explained both the differences and similarities without overcomplicating it. Great read 👍
The article explains VPN and DPN in a very clean and understandable way. I enjoyed the balanced comparison between both technologies. The privacy and security points were clearly highlighted. It’s a good learning resource for beginners. The writing is smooth and professional. Very informative overall.
You covered the governance aspect of decentralized networks beautifully. Transparency and trust are crucial — and you captured that perfectly.
This post made me rethink VPN usage entirely. The DPN model’s emphasis on user autonomy really stood out.
Great piece! I especially appreciated your note about how DPNs improve resistance to single-point failures.
Very well explained. I always thought VPNs were the only privacy option, but now I see how DPNs differ under the hood.
Really informative post. I’ve used VPNs for years, but this gave me a fresh perspective on DPNs and their future.
Really strong analysis. I’ve read dozens of VPN guides, but this is the first to properly contextualize DPNs as a network paradigm shift.
Loved your point about data control — DPNs truly shift power back to users.
This blog explains VPN vs DPN in a very clear way. I finally understand how decentralized networks really work. Great job!
Nicely done! I learned more from this one article than from a dozen Reddit threads.
Informative and easy to read. I didn’t realize DPNs could be so different from VPNs in a decentralized setup.
Really informative read! I hadn’t fully grasped the difference between VPN and DPN before. The comparison in decentralized networks was easy to follow. Very useful for anyone learning about network privacy!
Really enjoyed this breakdown. You explained VPN vs DPN in a very simple way without making it too technical. The decentralized angle was especially helpful.
Superb write-up. Would love to see you test some real-world speeds next time!
Simple words, strong message. This explained the real difference perfectly.
I love how you explained security and privacy in decentralized networks. Very helpful content!
Really cleared things up! I had no idea DPNs could be more secure than VPNs in some cases. Great breakdown for beginners and pros alike.
This article made the VPN vs DPN topic way easier to digest. Loved the part about security and speed trade-offs!
Really enjoyed this. Explaining the difference between server-based and node-based networks made everything clearer.
Helpful read! The section on real-world applications, like working in censorship-heavy regions, made it very practical.
I found your description of data sovereignty fascinating. You really highlighted why decentralization matters for user control.
Simple and direct — exactly how a tech article should be. Well done!
Interesting take! I’d love to see more about how DPNs handle encryption compared to traditional VPNs.
Good stuff! Would love to read a follow-up post comparing actual DPN services available today.
Very sharp insights! The way you connected decentralization, transparency, and privacy principles was first-rate.
Really clear article! I had no idea DPNs could offer both speed and privacy. The examples make it easy to understand the practical benefits over VPNs.
Excellent content as always. You make cybersecurity topics approachable without oversimplifying.
I really liked the focus on transparency and user control. It’s what makes decentralized models so powerful.
Great article. The decentralization angle is what sold me. Feels like a more “internet-native” solution than traditional VPNs.
Hands down the cleanest tech blog I’ve found in years. No clickbait, no fluff, just proper benchmarks and honest prices. Subscribed instantly.
Well balanced and fair. Some blogs overhype DPNs, but you kept it realistic.
This was such a refreshing read. You’ve managed to make complex tech sound accessible. Kudos!
Brilliant technical clarity. The way you described node consensus made the security model easy to follow.
This post is extremely helpful for anyone trying to understand modern network security. The comparison between VPN and DPN was logical, detailed, and practical. I really appreciate the effort put into this article.
I found the latency analysis fascinating. You made a strong case for how decentralization can balance speed and anonymity.
This has me thinking — could DPNs one day replace VPNs entirely
Your point about DPN scalability being naturally embedded through peer participation was brilliant. Great insight!
Excellent depth. The architecture diagram made the contrast between VPN tunnels and DPN paths immediately clear.
Loved the contrast between privacy and performance trade-offs. This is exactly the kind of discussion we need more of online.
I’d love to see you cover the energy costs of DPN networks next time. Great post though!
Fantastic article! Makes it easy to see the differences and similarities between VPNs and DPNs.
Very informative article! I’ve used VPNs for years but didn’t really understand how DPNs work. This cleared it up nicely.
I like how you explained the decentralized structure of DPNs. Makes me rethink my reliance on VPNs.
This article perfectly bridges the gap between theory and implementation. DPNs definitely sound like the next step forward.
Interesting read! I hadn’t realized DPNs offer better resilience than VPNs.
Short, simple, and very informative. The difference between VPN and DPN is now crystal clear to me.
Fantastic breakdown! I was always confused about the difference between VPN and DPN, but this article explains it logically and clearly. The network scanning basics section was especially helpful, and the diagrams and examples made it very easy to follow. I now understand why DPNs can be better in decentralized networks, and the beginner-friendly tips are great. This guide will definitely help me protect my network more effectively, and I highly recommend it to anyone interested in cybersecurity.
Great article! I never really understood the difference between VPN and DPN before reading this. The guide makes everything simple and easy to follow. The examples are practical and relatable, which helped me see the real-world applications. I now feel more confident about choosing the right tool for securing my network. Thanks for breaking it down so clearly.
Thanks for the clear comparison. I appreciate the explanation of encryption differences.
I appreciate the balanced view—many posts just push DPNs as superior without explaining limitations.
Well explained! The examples really helped clarify how VPNs centralize traffic versus DPNs distributing it.
I’ve been trying to figure out the practical differences between VPN and DPN for ages. This blog made it simple and easy to digest.
I appreciate how this blog goes beyond basic definitions and actually explains how VPNs and DPNs function in a decentralised network. The privacy and security comparison was particularly helpful. Definitely a useful read for anyone exploring decentralised tech.
Such a well-written article! I’ve read a few posts on VPNs before, but this one goes deeper into the differences while keeping it simple.
Informative piece. I now understand why DPNs can have lower trust risks than traditional VPNs.
Excellent points about transparency. A decentralized network can’t hide logs easily — that’s powerful.
Nicely balanced discussion. You covered performance, privacy, and practicality equally well.
Very helpful! I was confused about routing in DPNs vs VPNs, and this clarified it perfectly.
Awesome article! The section on decentralized networks was super clear. Now I actually understand why some people prefer DPNs over VPNs. Thanks for sharing!
Excellent breakdown of similarities and differences. This helped me choose the right solution for my needs.
I like the emphasis on decentralization. Feels like DPNs are the future for privacy-conscious users.
Interesting comparison. I wonder how scalable DPNs will be as more users adopt them.
I never realized that DPNs could distribute traffic across multiple nodes. Makes me wonder if they’re safer than VPNs for sensitive work.
Your explanation of decentralized data routing in DPNs was outstanding. It’s rare to find such clarity in a technical article.
I’m so glad you mentioned data ownership. That’s a crucial distinction between the two.
I liked your note about user incentives in DPN ecosystems — it shows real understanding of the underlying token-based frameworks.
Great article. The similarities section was really useful—I didn’t realize both encrypt traffic, just differently.
This was a solid read. The similarities section helped me see where both technologies overlap in real-world use.
Balanced write-up. Many articles overhype DPNs without mentioning practical limitations.
Brilliant analysis! I like that you didn’t shy away from DPN limitations either.
The privacy vs speed trade-off explanation was very helpful. I’m considering a DPN for my freelance projects now.
The explanation of VPN and DPN differences in this blog is clear and very well structured. It highlights how decentralization changes privacy and security in a practical way. I appreciated how the similarities were also covered instead of only focusing on differences. Overall, this is a strong and valuable article for anyone exploring decentralized networks in 2026.
Your example of decentralized routing really helped me grasp the technical side. Thanks for simplifying such a complex topic!
Nicely laid out and very accessible. I’m impressed at how you simplified such a tricky topic.
Loved how easy this was to read. The decentralised network section was especially helpful for beginners.
Excellent insights. I appreciate how you explained the peer-to-peer model of DPNs — it cleared up a lot of confusion about decentralized routing.
The diagrams explaining routing were excellent. Made the concepts much easier to grasp.
Brilliant explanation of decentralized networking. I liked how you kept it balanced instead of favouring one over the other.
I always thought VPNs were the only solution. Now I see DPNs have unique advantages.
Brilliant post — practical examples made the theory so much easier to follow. This should be a go-to reference for network engineers.
Nice breakdown! I especially liked the decentralized network examples. Makes the tech side much clearer for beginners.
I use both VPN and DPN networks and agree with your assessment. DPNs are still early but show massive potential.
Great write-up. I hadn’t thought about the implications of central servers before reading this.
very informative article and easy to read.
Good point about legal considerations. Decentralized networks can still face regulatory issues.
Insightful! The trust factor alone makes DPNs sound so much more appealing.
Loved your explanation of node-to-node encryption. Many people confuse it with VPN tunnelling.
Fantastic article! I liked how you broke down complex technical terms into easy-to-understand language. I’ve been wondering about the best privacy solution for my online activities, and now I feel more informed. The side-by-side comparison was very helpful, and I can see myself referring back to this guide often.
Very informative piece! The conclusion neatly tied everything together — VPNs aren’t obsolete, but DPNs clearly push the evolution forward.
Your explanation of how decentralized routing mitigates traffic bottlenecks was excellent. Very forward-thinking approach to network architecture!
Brilliant breakdown, mate! Finally someone explained why DPNs like Mysterium or Sentinel are actually faster for streaming when you’re on a decentralised node. Used a traditional VPN for years, but after reading this I’m switching to a DPN for my remote work in London. Cheers!
Top article. As a Brit working in fintech, the centralised point-of-failure on most VPNs always worried me. The latency charts you showed for DPNs in Europe are spot on – I’m seeing sub-40 ms to Frankfurt nodes on Deeper Network. Keep it up!
Рабочее зеркало джой казино обеспечивает стабильный доступ <a href=
https://joy-games.space/
Brilliant comparison! It’s amazing how DPNs are solving centralized weaknesses that VPNs still struggle with.
Really enjoyed this post! Very informative and easy to follow. Thanks for sharing!
This is one of the most thorough explanations I’ve read on VPNs vs DPNs. I especially liked how you broke down the differences in decentralized networks. The practical examples made it much easier to understand. I had no idea DPNs offered so much privacy. The security comparison section was really eye-opening. I’ll definitely consider using a DPN for my remote work setup. Great job on making a complex topic so accessible!
I enjoyed your explanation of how decentralization enhances trust through transparency. That’s the missing piece most people overlook.
Very helpful! I’ve been deciding whether to switch tools for remote work. This clarified a lot.
Fantastic content! I liked that you discussed both privacy and governance layers — something rarely covered in similar posts.
Interesting read! I’d love to see a follow-up post about performance differences in real-world scenarios.
This piece helped me visualize how decentralized infrastructure could change the way we manage online identities.
Really engaging read. I learned a lot about peer-to-peer encryption methods!
Very clear and informative article. I now understand how VPNs and DPNs differ and why each has its own advantages. The security comparison section was especially helpful, and I liked that it was short, easy to follow, and beginner-friendly. The examples made everything practical and easy to apply. Overall, this is a well-written and insightful guide for anyone interested in network security.
The difference between VPN and DPN is now crystal clear, and I especially liked the focus on decentralized networks. The guide is concise yet informative, making it easy to grasp even for beginners. I also appreciated the practical examples, which helped solidify my understanding. Overall, it’s a very useful article that I’ll be coming back to.
Thank you! This finally helped me understand why DPNs are being mentioned in blockchain forums.
Interesting comparison. Didn’t realise decentralized networks could be this secure. Thanks for the insights!
I’ve been exploring DPN tech lately — your blog filled in so many gaps, especially around encryption redundancy.
This post clarified a lot about how decentralized privacy networks maintain speed without compromising safety.
Clear and concise. You explained decentralization better than half the tech YouTubers I follow!
Informative piece. I appreciate how you highlighted performance differences. Latency is something I always struggle with on VPNs.
This is the first article that explained the VPN vs DPN difference without jargon. Short, clear and honestly very helpful.
You clearly understand both the network and human sides of the privacy debate. Great analysis overall.
Well explained! The way you outlined the evolution from VPN to DPN felt both logical and forward-looking.
Your explanation of node-to-node encryption in DPNs was excellent. Many people confuse it with standard VPN tunnelling.
Really enjoyed how you linked DPNs to the larger movement toward Web3. The future of network privacy is clearly heading that way.
Short and informative blog. The privacy discussion around VPNs vs DPNs was especially interesting. Looking forward to more tech comparisons like this.
Cool article! I’ve been confused about VPNs and DPNs for ages, but this helped me see the practical differences in real-world setups.
Your discussion on performance trade-offs between DPN and VPN systems was spot on. Excellent analysis and structure.
Launch into the massive sandbox of EVE Online. Become a legend today. Explore alongside thousands of explorers worldwide. Start playing for free
Excellent post! The comparison of routing methods in VPNs and DPNs was very clear and concise.
Very insightful! Makes me rethink how I use VPNs and consider DPNs for certain tasks.
Great post! The differences and similarities are laid out really well. Learned a lot about decentralized networks.
I appreciate the practical examples of using VPNs and DPNs in a decentralized network. Very well written and easy to follow.
Helpful breakdown! I finally understand why DPNs are becoming more popular in decentralized networks.
Super helpful post. I’ve been trying to understand VPNs versus DPNs for a while, and this article explains their similarities and differences very clearly. I particularly liked the practical scanning examples and the tips on network security. The language is approachable and beginner-friendly, which makes it much easier to follow. I now feel more confident about using these tools in real scenarios and can see the benefits of DPNs for privacy. This is exactly the type of guide I needed!
Excellent insight! Your point about tokenized incentive models for DPN nodes was spot on — very forward-looking.
Fascinating topic. Are DPNs already mainstream or still experimental?
Great post! I now understand why DPNs are considered more censorship-resistant than traditional VPNs.
Your performance evaluation was spot on. DPNs offering resilience without single-server dependency is revolutionary.
Fantastic post. VPNs might still win on simplicity, but decentralized options are looking more promising every day.
Very helpful article. I’ve been hearing about DPNs lately and this clarified how they actually function compared to VPNs.
Top work. I’d love to see a version of this comparing specific VPN and DPN providers next time.
Fantastic write-up! I’ve been confused about DPNs, but this cleared it up completely.
This article cleared up a lot of misconceptions I had. I thought all network privacy tools worked the same way!
Thanks for this! The comparison of encryption methods between VPNs and DPNs was really enlightening.
Thanks for breaking this down. The similarities were helpful—didn’t know both tools encrypt traffic but work differently.
I must say, this article is fantastic! It explains complex concepts in simple language, which is great for beginners. The section on open ports and network scanning basics was particularly useful. I didn’t know DPNs could offer extra privacy over VPNs, and the diagrams really helped visualize the process. The step-by-step approach makes it easy to follow, and it’s perfect for IT professionals and students alike. I feel more prepared to secure my own network now. Highly recommend it for anyone interested in cybersecurity!
Excellent post! You made complex networking concepts easy to digest for beginners.
Excellent work. The piece captured how decentralization fundamentally changes the trust model — that’s the key takeaway.
Great comparison. I liked how you highlighted the decentralised trust model without overcomplicating things.
Very clear and easy to read. The explanation of decentralized networks was my favorite part.
This article does a solid job explaining both the similarities and the key differences between VPNs and DPNs. The decentralised angle was especially interesting.
Awesome read! The examples you gave really helped me understand decentralized networking better.
Your explanation of decentralized peer validation was brilliant. It really shows how DPNs solve the trust issues that VPNs still struggle with.
This made me rethink my current VPN setup. DPNs might be worth experimenting with in a decentralized environment.
VPNs are great but after reading this, DPN feels like the future!
Interesting read. Performance is my biggest concern—DPNs sound great but I hope they become more stable.
Jazz Cyber Shield has become my go-to blog for real cybersecurity learning.
Very informative. I liked how you explained the pros and cons of both technologies without being overly technical.
This blog perfectly explained how DPN enhances privacy through decentralization.
As someone working in cybersecurity, I can confirm — your take on decentralized trust models is absolutely accurate. Great piece!
I appreciated the clarity with which you covered encryption protocols. You clearly know your networking fundamentals.
Such a helpful read! Now I know which one is better for my remote setup.
Your comparison between centralized VPN providers and decentralized peer nodes was spot on. A very well-researched article!
I love how professional yet friendly the writing feels. Not too technical but still accurate.
The part about encryption redundancy in DPNs really caught my attention. You’ve managed to make a dense topic very readable.
You captured the essence of distributed security perfectly. The examples of node redundancy were very well chosen.
I’m new to networking, but this post made me feel like I actually understand something complex.
Does DPN work on all devices or only through specific applications?
Loved this! VPNs always felt limited to me. DPN sounds like the future, especially for censorship-heavy regions.
This was such an enjoyable read. I shared it with a few friends who are also into decentralized tech — they loved it too!
Such a great analysis. DPNs definitely seem like a more future-proof solution for privacy-conscious users.
Superb analysis! You managed to keep the technical detail without overwhelming the reader.
Really informative post! I didn’t realize how DPNs differ from traditional VPNs in decentralized networks. The explanations were super clear, and it helped me figure out which one I should use for better privacy. Thanks for breaking it down so well!
I like the section on decentralization benefits. Definitely makes DPNs sound more future-proof than VPNs.
Good comparison! I like that you didn’t oversell either technology and presented both strengths and weaknesses.
Really interesting comparison. I’ve used VPNs for years but only recently learned about DPNs—your explanation of decentralized routing makes it much clearer!
DPNs sound fascinating but I worry about scalability. Do they handle millions of users efficiently?
Really thoughtful comparison. I’m glad you didn’t just bash VPNs — both clearly have a place.
Excellent insights! I’ve been researching network privacy tools for a while, and this piece helped me see where VPNs still outperform DPNs in terms of stability.
This is the clearest comparison I’ve come across so far. Really appreciate your writing style!
Brilliant! I think DPNs still have a few years to mature, but the concept is solid.
Perfectly written and well-researched. You’ve turned a niche topic into something genuinely engaging!
You make a strong case for DPNs, but I still think VPNs offer better user support for now. Great discussion though!
Great write-up. I’d love to see more examples of DPNs currently available in the market.
I agree with you completely. MSI’s Gaming X Trio models have always been solid — quiet fans and rock-steady boost clocks.
Excellent comparison. The section about trust and transparency really stood out.
This is one of the best articles I’ve read on VPNs versus DPNs. The examples and explanations are very clear, especially regarding privacy advantages in decentralized networks.
Excellent explanation! I’ve always used VPNs but had no clue how DPNs actually decentralize network traffic.
Great write-up. I didn’t realize DPNs don’t rely on central servers. That seems like a big advantage for privacy.
Great article! I found the comparison between VPN and DPN really clear and insightful. The way you explained their differences and similarities in decentralized networks helped me understand which solution might work best for my small business.
The decentralized model seems like the logical next step for privacy-conscious users.
Nicely written. I’ve used VPNs for years but DPNs sound like the future of private networking.
I’ve always wondered how DPNs handle traffic distribution. Your explanation made it a lot easier to understand.
This is a solid explanation. I like how you highlighted both the pros and cons of VPNs and DPNs.
Very well structured article. The similarities section was just as useful as the differences. Clear, modern and relevant.
This article helped me understand the real differences between VPN and DPN. I was always confused about which one to use for secure work. Thanks for the clear explanations and examples!
Super clear comparison. I now understand the real benefits and trade-offs between VPNs and DPNs.
Great article! I liked how you compared VPNs and DPNs side by side. It made it easy to understand the pros and cons of each, especially in decentralized setups. I’ll definitely be coming back to Jazz Cyber Shield for more tech guides like this.
This was a great comparison of VPN and DPN. I finally understand how decentralization changes online privacy.
Very insightful! The section on legal considerations and data privacy was a nice touch.
Short, sharp and informative. I liked how you compared privacy, control and infrastructure side by side. Makes choosing between VPN and DPN much easier.
Really clear explanation! The section about DPNs reducing single points of failure was eye-opening.
interesting breakdown.
Super clear and actually fun to read. Didn’t expect to understand DPNs this easily. You nailed it!
Great read. I liked how you highlighted both security and performance trade-offs between VPNs and DPNs.
Excellent article! I’ve always been a bit lost when it comes to VPNs versus DPNs. Your explanations were clear and easy to follow, even for a beginner like me. I especially liked the examples showing real-world applications, which made it much easier to understand the concepts. This has definitely helped me make smarter choices for my network setup.
This was a very informative comparison. I liked how you covered both similarities and differences while keeping the focus on decentralisation and user privacy. It’s refreshing to see a topic like this explained in a straightforward and practical way.
I didn’t know DPN worked like this. Thanks for the simple and direct explanation.
Very informative and well-explained blog. The comparison between VPN and DPN is clear and easy to understand, making it a great resource for anyone learning about decentralized network security.
Your explanation of VPN vs DPN was honestly the clearest I’ve read so far. I liked how you compared the security layers without making it overly technical. The real-world examples really helped me understand when a DPN is actually more useful. Great breakdown—keep writing more like this!
Really enjoyed this breakdown! I never knew DPNs could offer that level of decentralised protection. Super clear comparison!
Really useful insights.
This post is really helpful. I was confused about decentralized networks for a while, but the comparison between VPNs and DPNs is clear and well-structured. I especially liked the part about security risks and privacy, and the practical examples made it easier to understand. It’s a guide I’ll keep referring back to because it’s beginner-friendly and straight to the point. Learning about DPNs was a nice bonus, and I look forward to applying these tips soon.
This is exactly the guide I needed. The pros and cons section helped me decide which tool to try first, and the focus on decentralized network security was excellent. The practical scanning tips are easy to follow, and I now feel more confident managing my network safely. The article is written clearly without jargon, making it perfect for beginners. The examples really help concepts stick, and I’m looking forward to more posts like this.
Brilliant explanation! I never realised how different a DPN is from a VPN. The examples you gave really helped me understand it in the context of decentralized networks.
This cleared up a lot of confusion for me. The section explaining how decentralized nodes work was especially useful. Nicely written and easy to follow!
Massive fan of this! I’ve been looking into DePIN tech lately, and your breakdown of how a DPN removes the “middleman” VPN provider is spot on. Proper insight.
Brilliant read. The bit about DPNs having no central point of failure is exactly why I’m making
Cracking post. The similarity in encryption is there, but the decentralized node aspect of a DPN is clearly the future for privacy. No more logs to worry about!
Quality stuff. Most people just think “VPN” is the only way, but working in a decentralized network really needs that peer-to-peer security a DPN offers.
Spot on comparison. I never realized DPNs could actually save you money in the long run since there’s no monthly sub to a massive corporation. Top tier content.