The rapid evolution in the cybersecurity landscape poses increasing threats to businesses from increasingly sophisticated attacks. Therefore, a thorough understanding of Next-Generation Firewall (NGFW), Threat Intelligence, and Zero Trust framework differences is essential for protecting critical assets. In this article, we will first explain the individual technologies in detail, then compare their functionalities among them, and consequently help you identify the optimal strategy pertaining to your organization.
What Is a Next-Generation Firewall (NGFW)?
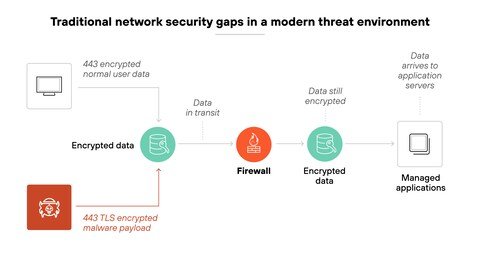
A Next-Generation Firewall (NGFW) defines itself more than a traditional firewall– it integrates stateful inspection, intrusion detection, and application awareness. Unlike legacy firewalls, NGFWs can analyze traffic at the application layer, making a decision based on the context, not just IP addresses.
In addition, NGFW systems integrate Threat Intelligence feeds for identifying malicious behavior in near real-time. This proactive approach reduces the chances of a successful breach while also ensuring that enterprises are ahead of their adversaries. Furthermore, enterprises can also deploy NGFWs to segment networks such that lateral movement of threats is restricted should any breach occur.
Threat Intelligence Explains
Threat Intelligence is the gathering, interpreting, and using information on what could be or is available on cyber threats. Using threat intelligence, a company can be able to predict the attacks and make its fortifications and also prioritize dangerous vulnerabilities.
In addition, threat feeds are a repository of actionable insights on malware types, phishing campaigns, and zero-day exploits. Consequently, IT teams will respond more swiftly, cutting down on depreciation time while also avoiding costly data breaches. Joining ngfw with threat intelligence thus affords a layered security perspective that integrates prevention, detection, and mitigation.
What is Zero Trust?
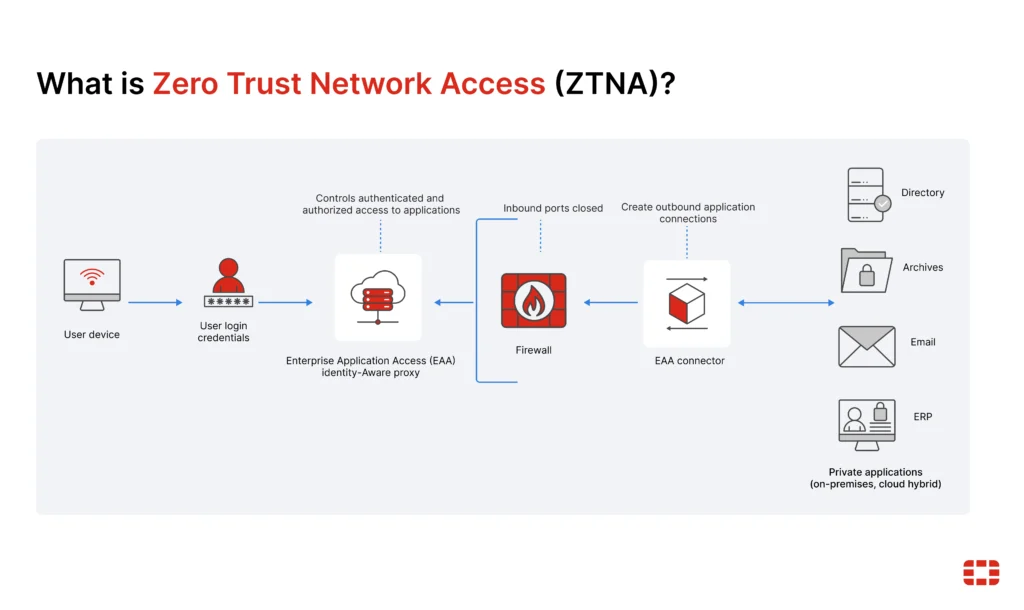
Zero Trust is a model of security that rests on “never trust, always verify.” So unlike perimeter security, which assumes that the threats are only external, the Zero Trust architecture believes that a threat exists internally as well. Hence the users, devices, and applications must authenticate themselves as well as authorize themselves before they can access any resources.
In addition, Zero Trust enforces micro-segmentation coupled with access least-privileges, thus minimizing possible breach impacts. Thus, even when an intruder gains access to a segment of the network, lateral movement becomes limited. Zero Trust, combined with NGFW and threat intelligence, provides an organizations complete multi-layered security.
Differences Between NGFW and Threat Intelligence, and Zero Trust
Although NGFW, Threat Intelligence, and Zero Trust improve cybersecurity in specific ways, they all address different concerns:
- NGFW: Application-aware adaptive mechanisms for intrusion prevention, traffic inspection, and firewall policies.
- Threat Intelligence: Actionable insights for anticipating or preventing attacks.
- Zero Trust: Stricter access control and continuous user verification and device access without exception.
And they complement each other. NGFWs are enforcement layer, threat intelligence adds context, and Zero Trust governs access policies. Thus, these three are truly comprehensive and the ultimate defense against advanced cyber threats.
Innovative New Services from Businesses
In their pursuit of security-mandating new generation firewalls, deploying threat intelligence systems, and making robust the zero-trust principle, businesses begin to harvest a few of the benefits cited below:
- Improving security posture: Each of the defenses addresses unique attack vectors.
- Minimized impact from breaches: Micro-segmentation and threat intelligence lower exposure.
- Attack prevention: Real-time insights and automated reactions prevent the very attack from succeeding.
Fortified in this manner, the technologies then provide security that is both strong, scalable and adaptable by the latest demands of cybersecurity.
Conclusion
Understanding the differences between NGFW, Threat Intelligence, and Zero Trust is essential for enterprises looking to build a solid cybersecurity framework. Each technology promises benefits on its own, but the whole is indeed greater than the sum of its parts, as part of a comprehensive protection strategy that will safeguard critical assets and put operations out of harm’s way. Therefore, organizations should assess their security requirements, invest in the right technologies, and put in place layers in order to shield against emerging threats in cyberspace.



Great breakdown of NGFW, Threat Intelligence, and ZeroBlog comment creation Trust—three terms that often get used interchangeably but serve very different roles. What stood out to me is how NGFW acts as the frontline defense, while threat intelligence provides the context, and Zero Trust ties it all together with a strategic framework. It would be interesting to see more discussion on how these approaches can complement each other in layered security rather than being viewed in isolation.