With the advent of modern connectivity, firewall rules have come to be considered one of the rudimentary components in network security. They help organizations and individuals decide what applications are allowed to access the Internet and which applications must be blocked. Due to the rise of cyber threats, the proper configuration of firewall rules keeps sensitive information safe. Furthermore, configuring properly means trade-offs between security and performance of applications. Thus, learning how to set firewall rules for allowing or blocking applications becomes an essential skill for IT professionals and small-business owners.
What Are Firewall Rules?
Firewall rules are instructions for the system as to which traffic can pass and which must be denied. They are like filters for everything leaving or entering your machine with the Internet. For instance, you can set up a rule to allow Microsoft Teams to connect while blocking a nefarious program from connecting to your network. The other aspect of the rule is that it applies to any inbound traffic to your system and the outbound traffic would mean anything leaving your system. Thus they even guard you from malware, data loss, and hacking attempts.
What is the point of setting Firewall Rules for Applications?
That is the purpose of configuring firewall rules, since access should differ for different applications. For instance, enable necessary applications that are business-critical like Zoom or Slack to always have constant connectivity. Block irrelevant programs that do not serve any purpose, might consume bandwidth and could pose security risks. This consequently reduces bandwidth usage and creates healthier network conditions. Strong firewall policies thus lead to better security and productivity for companies.
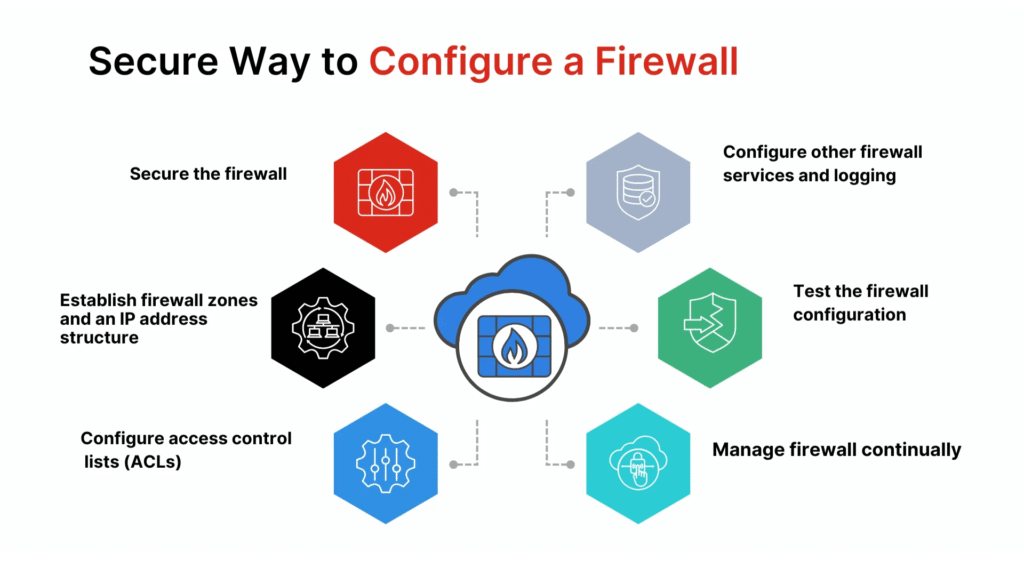
Step-by-Step Guide to Allow or Block Applications
1. Access the Firewall Settings
First access the firewall configuration tool on your device-the windows-based access is through Control Panel->System and Security->Windows Defender Firewall. Then click on Advanced Settings from the resultant page that shows you the inbound and outbound rules.
2. Create a New Rule
Then choose one between inbound or outbound rule. Select New Rule and choose Program. This way, you would be able to specify the application to allow or block.
3. Choose Application Path
Then browse through the application executable file (.exe). In this case, if you want to allow Google Chrome, select its program file.
4. Set the Action
Next, decide whether you want to allow or block the connection. Allowing means giving the app network access, while blocking means stopping the app from sending or receiving data.
5. Save the Rule and Test
Finally, name the rule so that you can easily recognize it, and then save it. Launch the application and test it. If the application is blocked, it won’t connect; if it’s allowed, it should run normally.
Common Uses for Firewall Rules
- Block suspicious programs- Prevent malware from communicating with external servers.
- Allow tools that are critical to business- Help ensure the smooth functioning of things like Zoom, Outlook, and Teams.
- Restrict bandwidth-hogging applications- Limit streaming or gaming apps inside corporate environments.
- Prevent sensitive data theft- Blocking unauthorized applications from accessing databases sitting within the company.
This way that the rules can be tailored to different situations means that the organization is able to exert precise control over the operation of its networks.
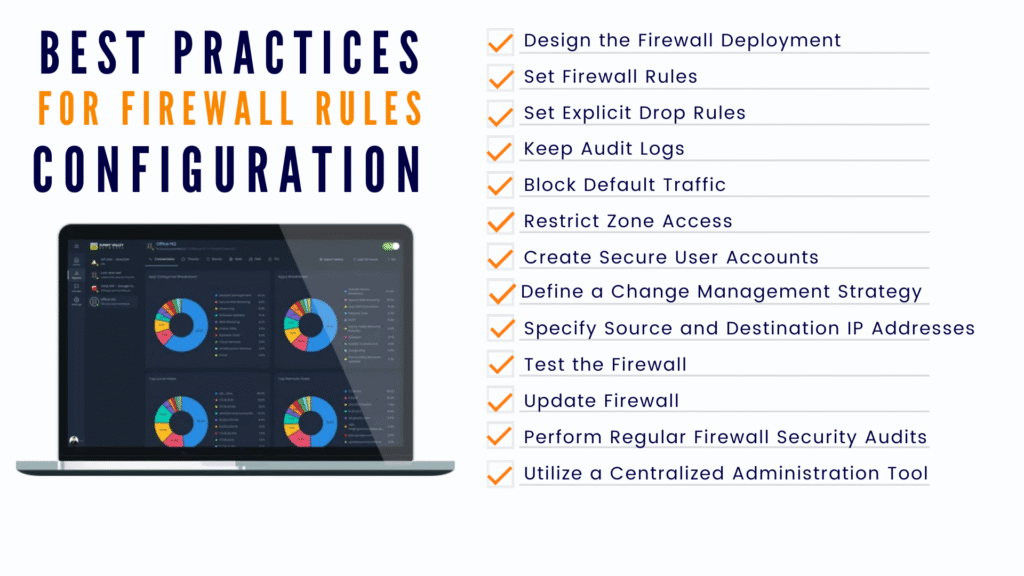
Best Practices in Configuring Firewall Rules
- Least privilege principle – Permit only the applications that are necessary.
- Update rules regularly – Delete disused or unused app rules.
- Log and report activity – Monitor which apps try to get access without permission.
- Antivirus integration – House additional layers along with that.
Documents also constitute your firewall strategy, so that they can keep the IT teams in check, staying ahead.
Conclusion
Thus, configuring firewall rules is probably one of the most effective methods for controlling the access applications inflict on your network. People and companies know that this can be learned, so as to allow and prevent applications, information remain secure but work continues. The technical side of the process can be somewhat discouraging, but a step-by-step review makes it workable. Firewall configuration does not only involve security but also a rather important process today for the digital society.



Great breakdown of how firewall rules work. One thing I’ve noticed is that people oftenDigital Marketing Blog Comment forget to review their rules regularly—over time, outdated rules can create unnecessary risks or even block critical apps unintentionally. Setting a schedule to audit and update firewall rules can really strengthen overall security.